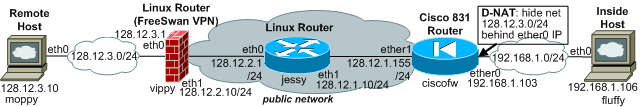
Network Layout
Introduction

Pictured left: Cisco's 831 Router for firewalling and optional hardware-accelerated VPN connectivity, incl. site-to-site VPN (2MB/s 3DES). Motorola RISC CPU, 64MB RAM, 12MB Flash. See here fore a view [inside]
Introduced at the end of 2002, the Cisco 831 SOHO router is competing with the smaller, faster and easier configurable PIX 501 of Cisco's own making. Altough released one year after the PIX 501, with more then twice the physical size and housed in cheap plastic, are there any advantages? Well, if having a full-fledged Cisco IOS at your fingertips is one, than thats it. We will configure the 831 identical to the PIX site-to-site IPSEC VPN setup with NAT.
First, we wipe out any old setings and load the latest IOS software image. With a serial cable to the Routers console port and the minicom program under Linux, we send a 'Break' signal to the device right after power-on. The 'Break' signal is usually a special command sequence in the terminal program, I had to start minicom with -m to use 'ALT' as the meta key in order to generate the 'Break' sequence with 'ALT+F'. At the ROM prompt, we reset the configuration with the command 'confreg 0x2142', followed by a 'reset'. The device reloads with a empty configuration.
Setting up the Cisco 831 Router
Before we start, we factory-reset the router and also clear the enable password.
unknowncisco>sho ver (skipping output to last line...)
... Configuration register is 0x2102
unknowncisco>
System Bootstrap, Version 12.2(11r)YV3, RELEASE SOFTWARE
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 2004 by cisco Systems, Inc.
C800/SOHO series (Board ID: 29-129) platform with 65536
Kbytes of main memory
rommon 1 > confreg 0x2142
You must reset or power cycle for new config to take effect
rommon 2 > reset
.. (another boot sequence later...)
Router>enable
Router>conf t
Router>config-register 0x2102 (set the config back to original)
Router>copy run start (this overwrites the old config)
Router⧁reload [y]We set the hostname, the interface IP's, enable the interfaces and routing, set the default route to the outside and finish configuring SSH device management:
Router#conf t
Router(config)#hostname ciscofirewall
ciscofirewall(config-if)#no ip domain-lookup
ciscofirewall(config-if)#interface Ethernet1
ciscofirewall(config-if)#description outside
ciscofirewall(config-if)#ip address 128.12.1.155 255.255.255.0
ciscofirewall(config-if)#no shutdown
ciscofirewall(config-if)#exit
ciscofirewall(config)#ip routing
ciscofirewall(config)#ip route static inter-vrf
ciscofirewall(config)#ip route 0.0.0.0 0.0.0.0 128.12.1.10
ciscofirewall(config)#enable secret test
ciscofirewall(config)#ip domain-name frank4dd.com
ciscofirewall(config)#aaa new-model
ciscofirewall(config)#username cisco secret 0 cisco
ciscofirewall(config)#crypto key generate rsa general-keys modulus 1024
The name for the keys will be: ciscofirewall.frank4dd.com...
ciscofirewall(config)#exitNow we check if routing is okay and ping works.
ciscofirewall>sho ip int brief
Interface IP-Address OK? Method Status Protocol
FastEthernet1 unassigned YES unset up up
FastEthernet2 unassigned YES unset down down
FastEthernet3 unassigned YES unset down down
FastEthernet4 unassigned YES unset down down
Ethernet0 192.168.1.103 YES manual up up
Ethernet1 128.12.1.155 YES manual up up
Ethernet2 unassigned YES NVRAM administr. down down
ciscofirewall#sho ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is 128.12.1.10 to network 0.0.0.0
128.12.0.0/24 is subnetted, 1 subnets
C 128.12.1.0 is directly connected, Ethernet1
C 192.168.1.0/24 is directly connected, Ethernet0
S* 0.0.0.0/0 [1/0] via 128.12.1.10Our first Cisco 831 config for basic routing is here. The issued commands for copy & paste are here.
Configuring a IPSec VPN on the Cisco 831

Pictured left: Cisco 831 back side with 4-port FastEthernet switch, serial console port and outside 10MB/s interface Ethernet1.
First we generate a access list 102 to define the traffic that should go into the VPN tunnel. Next, we define the parameters of the ISAKMP security association, consisting of a policy and key information used in phase 1 of the ISAKMP negotiation process.
access-list 102 permit ip 192.168.1.0 0.0.0.255 128.12.3.0 0.0.0.255
crypto isakmp policy 1
encryption 3des
hash md5
authentication pre-share
group 2
exit
crypto isakmp identity address
crypto isakmp key dobsekred address 128.12.2.10
crypto isakmp enableThen we set the encryption parameters in ISAKMP phase 2, used for negotiating the settings of the IPSEC security association.
crypto ipsec security-association lifetime seconds 28800
crypto ipsec transform-set myset esp-3des esp-sha-hmac
mode tunnel
exitThe access list, encryption settings and VPN peer data are now combined into a crypto map "mymap". Finally, we bind this map to the outside interface Ethernet1.
crypto map mymap 10 ipsec-isakmp
set peer 128.12.2.10
set security-association level per-host
set transform-set myset
match address 102
exit
interface Ethernet1
crypto map mymap
exitOur Cisco 831 3DES VPN configuration is here. The issued commands for copy & paste are here. Cisco's debug command can be used to monitor the VPN tunnel establishment in detail.
debug crypto isakmp
debug crypto ipsec
show logAn example debug of a succesfully established connection is here. Good housekeeping settings (enable SSH, no CDP, set Logging) are here.
Configuring the Linux FreeSwan VPN
Here we use almost identical settings as in the previous PIX VPN setup here. The updated ipsec.conf is here, the ipsec.secrets file here. Troubleshooting the Linux side can be done via the standard logs in /var/log/messages. From the two FreeSwan daemons Pluto (responsible for IKE/ISAKMP) and KLIPS (IPSEC transport), Pluto can send debug information to a log file. It goes per default to syslog, using daemon.error as the log facility/priority. A sample output is shown below.
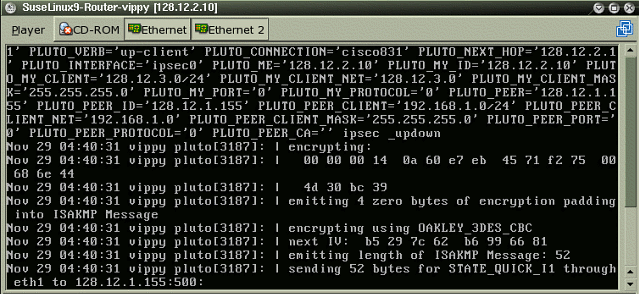
Adding inbound NAT to our VPN connection

We add a simple access list defining the network we want to do NAT for. Then we define the NAT rule, describing we want to NAT the source of the packets coming from 'inside', hide the packets behind the IP of the interface Ethernet0. Finally, we define the external interface Ethernet1 as NAT inside (were the packets come from) and the internal interface Ethernet0 as NAT outside (were the packets go).
conf t
access-list 1 permit 128.12.3.0 0.0.0.255
ip nat inside source list 1 interface Ethernet0
interface Ethernet1
ip nat inside
exit
interface Ethernet0
ip nat outside
exitThe updated Cisco 831 configuration is now here. The issued commands for copy & paste are here and 'show ip nat translations' verifies the NAT here.
Adding outbound NAT to our VPN Configuration
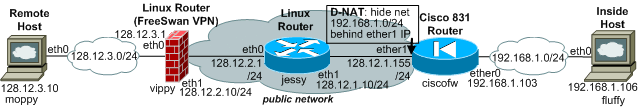
Now we convert the existing NAT rules for outbound NAT, hiding the internal network 192.168.1.0/24 behind the external interface Ethernet1. First, we change the access lists defining the NAT and VPN networks. Then we re-create the NAT rule, changing the interface from Ethernet0 to Ethernet1. Finally, we exchange the interface definitions for inside/outside NAT directions. The latest outbound NAT configuration is here The NAT commands for copy & paste are here and 'show ip nat translations' verifies the NAT here
Pinging from the internal host 192.168.1.106 to remote IP 128.12.3.10 works fine. However, trying to ping reverse from 128.12.3.10 reveals that these packets are passed on by the Linux VPN router in the clear, instead of being encrypted by the tunnel. Hence they reach the Cisco 831 router and are passed on to the internal host 192.168.1.106. The internal host replies, these packets are NAT'ed on the Cisco 831 router and send back through the VPN tunnel. In order to stop this unwanted behaviour and to satisfy basic security needs, we define a access list on the outside interface, allowing only incoming traffic for IPSEC and remote device management by SSH. Such a outside protection ACL should be applied regardless of NAT settings anyways.
conf t
access-list 100 permit icmp any host 128.12.1.155
access-list 100 permit esp host 128.12.2.10 host 128.12.1.155
access-list 100 permit udp host 128.12.2.10 host 128.12.1.155 eq isakmp
access-list 100 permit tcp host 128.12.2.10 host 128.12.1.155 eq 22
access-list 100 deny ip any any
interface Ethernet1
ip access-group 100 in
exitThis ACL allows ping (icmp) from any to the outside interface IP, IPSEC encrypted traffic (esp), the IKE key exchange over UDP/500 and finally SSH management access from outside (if absolutely necessary). With the current tunnel setup on the Linux side, defining 128.12.1.155 as the tunnel traffic, SSH from either 128.12.3.10 or 128.12.2.10 works only when IPSEC is stopped on the Linux VPN router ('/etc/init.d/ipsec stop').
Links and Literature:
- Cisco Systems: Cisco Router (800) Password Recovery Procedure Cisco Link , Local Copy (PDF) Link
- Cisco Systems: Cisco 831 Router Hardware Installation Guide Cisco Link , Local Copy (PDF) Link
- Cisco Systems: Cisco IOS Configuration Fundamentals Command Reference Cisco Link , Local Copy (PDF) Link